
Update: The title and content have been updated to clarify that this is a MiTM phishing attack carried out using Flipper Zero, but it can be carried out by other devices.
Researchers demonstrated how to perform a man-in-the-middle (MiTM) phishing attack to compromise a Tesla account and unlock and start a car. This attack works on the latest Tesla app version 4.30.6 and Tesla software version 11.1 2024.2.7.
As part of this attack, security researchers Talal Haji Bakri and tommy miske Register a new “phone key” that you can use to access your Tesla.
Researchers reported their findings to Tesla that the link between cars and new phones lacked adequate authentication security. However, the automaker deemed this report to be irrelevant.
The researchers used Flipper Zero to perform this phishing attack, but it can also easily be performed using other devices such as a computer, Raspberry Pi, or Android smartphone.
Phishing attack
Attackers at Tesla Supercharger stations could deploy a WiFi network called “Tesla Guest.” This SSID is commonly found at Tesla service centers and is well known to car owners.
Mysk used a Flipper Zero to broadcast a WiFi network, but says the same thing can be accomplished using a Raspberry Pi or other devices with WiFi hotspot capabilities.
Once victims connect to the spoofed network, they are presented with a fake Tesla login page that asks them to log in using their Tesla account credentials. Whatever the victim types on the phishing page, the attacker can see it in real time on her Flipper Zero.
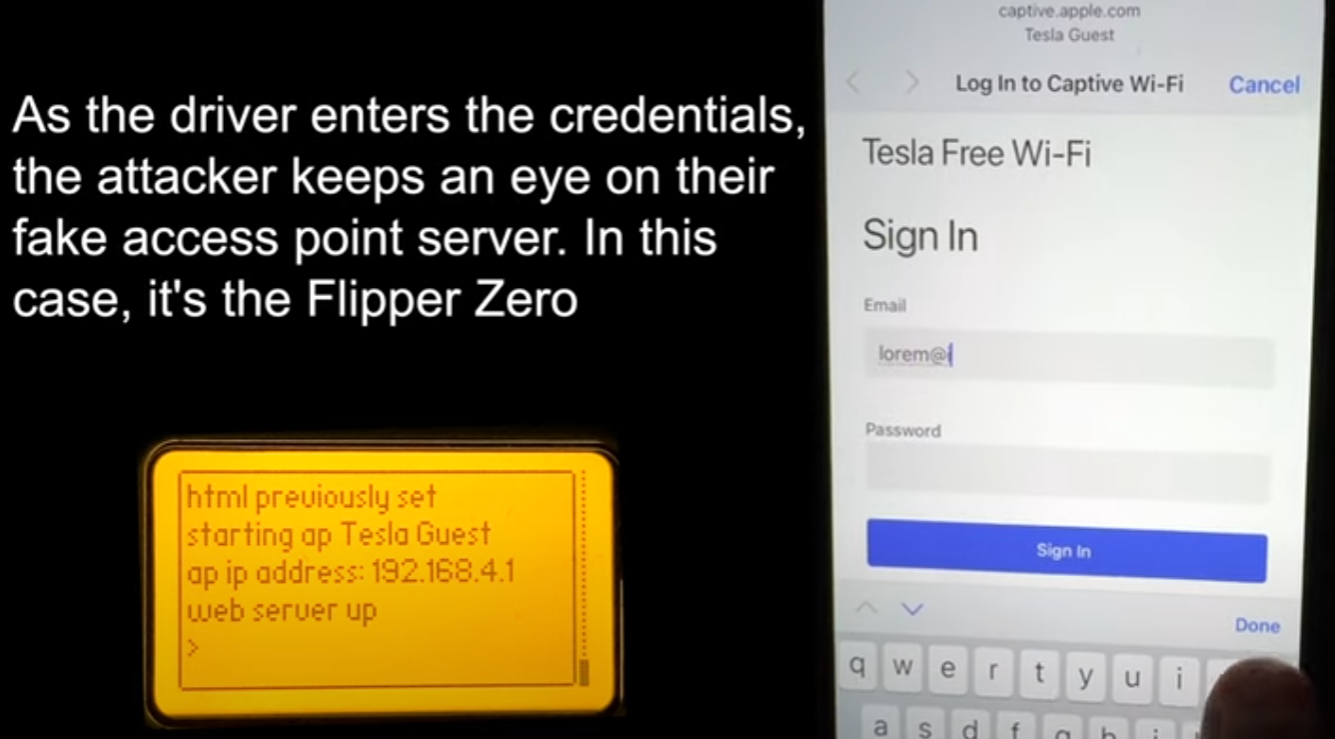
After entering Tesla account credentials, the phishing page asks for a one-time password for the account, allowing the attacker to bypass two-factor authentication protection.
The attacker must move on and use the stolen credentials to log into the Tesla app before the OTP expires. Once the account is compromised, the threat actor can track the vehicle’s location in real-time.
Adding a new key
Once they have access to the victim’s Tesla account, the attacker can add a new “phone key.” For this, you need to be very close to the car, just a few meters away.
Phone Keys uses Tesla’s mobile app in conjunction with a car owner’s smartphone, allowing them to automatically lock and unlock their vehicle via a secure Bluetooth connection.
Tesla cars also use key cards. This is a slim RFID card that must be placed in the RFID reader in the center console to start the vehicle. Although more secure, Tesla treats it as a backup option in case your phone key is unavailable or your battery dies.
Mysk says adding a new phone key through the app doesn’t require you to unlock your car or leave your smartphone inside, which creates a major security gap.
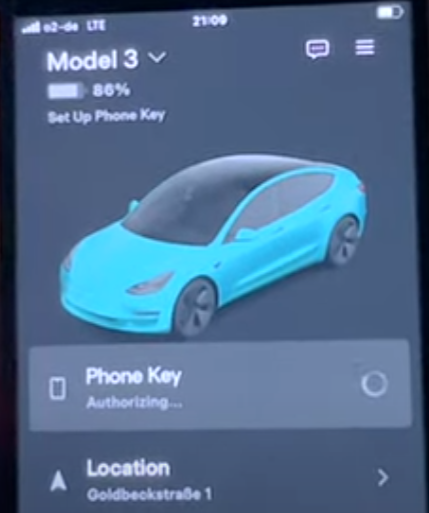
What’s worse, even when a new phone key is added, Tesla owners receive no notification of that fact through the app, and no warning appears on the car’s touchscreen.
With the new phone key, the attacker can unlock the car, activate all systems, and drive away as if he were the owner.
Mysk notes that this attack was successful on a Tesla Model 3. In a report to the car company, researchers say the hijacked Tesla account must belong to the primary driver and the vehicle must already be linked to a phone key. .
Researchers claim that requiring a physical Tesla card key when adding a new phone key improves security by adding a layer of authentication to new phones.
“I was able to add a second phone key to my new iPhone without the Tesla app prompting me to use my key card to authenticate the session on my new iPhone. I used a username and password for my new iPhone. “The phone key was activated as soon as I gave the app access to location services,” Tommy Misk and Talal Haji Bakri wrote in a report to Tesla. ing.
The company responded that an investigation determined this was intended behavior and that the Tesla Model 3 owner’s manual does not state that a keycard is required to add a phone key.
BleepingComputer reached out to Tesla with questions about the above and whether it plans to issue an OTA update that introduces security measures to prevent these attacks, but has not yet heard back.


