[ad_1]
With the growth of IoT devices and consumer smart gadgets, the world is pushing 4G networks to their limits. 5G not only offers faster speeds and higher capacity than previous cellular generations, it also offers improved security and privacy. 5G is essentially an evolution of his 4G security controls with new security protocols that address existing vulnerabilities.
This article describes the security architecture of 5G, how it differs from 4G, and the benefits and security challenges it brings.
5G security architecture
The 5G core network provides coordination between different parts of the access network and connectivity to the internet, and is a service-based architecture (SBA) built around cloud-based technologies, including authentication, security, session management, etc. provides the functionality of And the service.
SBA relies heavily on network function virtualization, which separates network functions into modular services and virtualizes network services that traditionally run on proprietary hardware. These are deployed using multi-access edge computing. Multi-access edge computing is a network architecture that places cloud computing and storage capabilities closer to users at the edge of the network.
Despite these changes, there is still a clear modular separation between the Radio Access Network (RAN) that provides wireless connectivity and the core security protocols.
Although 5G inherits much of the network security architecture of 4G, the 5G standard differs from previous standards in adopting security as a key design principle. For example, vendors and mobile carriers are required to comply with the requirements of the GSM Association Network Equipment Security Assurance Scheme. However, 5G, like 4G, will replace traditional network infrastructure because many new services and 5G technologies rely on virtualization, replacing specialized hardware with software-defined systems that work at the network edge. You can’t rely on security.
Therefore, 5G requires and supports more specialized security protocols and features to address the challenges of a significantly expanded attack surface and significantly increased use cases.
5G security features
With 5G, some of the most important security improvements are:
encryption
Stronger 256-bit encryption algorithms and separation of security keys between core networks provide better data protection and aim to make communications highly resistant to attacks by quantum computers .
privacy
In addition to strong encryption, the confidentiality and integrity of all data passing through the 5G network is protected, improving data privacy. Threats such as International Mobile Subscriber ID and Temporary Mobile Subscriber ID catchers allow 2G, 3G, and 4G networks to transmit a user’s permanent or temporary identifier in clear text during the device’s initial connection to the network. exploiting the fact that 5G networks make it impossible. .
5G security specifications do not allow plaintext transmission of Subscription Permanent Identifier (SUPI). Instead, 5G devices never transmit their real identity, but rather a privacy-preserving identifier containing a concealed SUPI called Subscriber Concealed Identity. This ensures that the identity and location of a user or device is encrypted, making it impossible to identify or locate them from the moment they join the network.
In addition to control plane integrity checks, 5G also adds additional checks to the user plane, which carries network user traffic between devices and the RAN. This ensures that messages between the device and applications on the user plane cannot be intercepted or modified over the air.
Authentication and authorization
5G has an authentication protocol called 5G Authentication and Key Agreement that uses asymmetric randomized cryptography to verify the identity of users, devices, and network elements. Its access and mobility management function sends the authentication request to the authentication server function, which forwards the authentication request to the unified data management and determines the appropriate authentication method depending on the subscriber profile. Although 4G supports pre-shared keys, certificates, and tokens, 4G requires a physical SIM card, which is not practical for simple IoT devices that rely on embedded SIMs.
roaming security
All communications between core network nodes use the same set of protocols protected by the same security controls, reducing the number of security processes. Security Edge Protection Proxy (SEPP) also implements end-to-end security protection for source and destination network traffic. SEPP replaces Signaling System 7 and Diameter used in 3G and 4G networks.
reliability
Network slicing, similar to traditional network segmentation, allows different segments to have security controls customized for specific use cases. Additionally, if an incident occurs, traffic can be immediately blocked or isolated if it is on a different network slice.
5G security benefits
5G introduces much-needed improvements to 4G network security with more frequent authentication and integrity checks. The fact that data can be transferred at high speeds using strong encryption complemented by authentication means that smart automation, better critical infrastructure monitoring, and smart cities are real possibilities.
The 5G standards incorporate input and expertise from around the world, and security is at the heart of it. With security controls built in at the design stage, 5G networks should be more resilient to current and future attacks.
5G security challenges
These benefits come at a price, as 5G deployments are expensive. For example, more transmitters are required to cover the same area as a 4G network, and security best practices increase costs. 5G will require strong enforcement by governments and compliance regulators such as the Federal Communications Commission to crack down on the omission of essential security features to reduce costs, which has led to security issues in many previous-generation networks. It has weakened it.
5G deployment relies on global supply chains, providing many opportunities for hackers to compromise hardware, software, and services. In fact, it will be several years before 5G networks that do not use legacy technologies become a reality. Until then, 5G must remain interoperable with his 3G and 4G. This means that downgrade attacks are a threat where hackers manipulate your connection to use a less secure 3G or 4G service.
There is a shortage of security professionals with deep knowledge of 5G security. While it is clear that vendors need to correctly implement the security controls required by the relevant standards, the greater risk is that mobile network operators actually deploying 5G will have to implement new or that it may introduce unforeseen risks or vulnerabilities. Unable to configure system correctly.
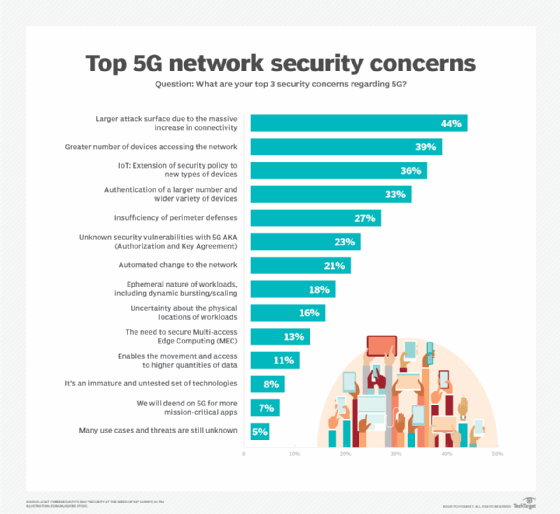
5G infrastructure is much more complex than 4G, with millions of connected devices, more traffic routing points, and a wider range of entry points, significantly increasing the attack surface. Monitoring and maintenance must be upgraded to maintain real-time threat detection. Otherwise, one malicious device could compromise thousands of nearby interconnected devices.
5G will expand connected services and industries with innovative use cases that could attract a new wave of cybercrime and threat vectors that will test the resiliency of 5G networks and the strength of controls that provide security for 5G communications. We support the creation of Many of these risks and security threats are still not fully understood. As a result, the Third Generation Partnership Project and other organizations involved in setting security standards for mobile technologies will ensure that the latest requirements are implemented based on the changing threat landscape and future risk assessments. is needed.
5G security due diligence
5G is beginning to change the landscape of the connected world we live in, becoming central to countless mission-critical processes and activities. This is why 5G security is a topic of discussion at both government and industry levels. In the world. Once fully deployed, 5G will significantly improve security compared to comparable 4G services, as long as it is deployed with end-to-end monitoring of system architectures, services, and devices in accordance with best practices and relevant standards. Masu.
Due diligence is essential for organizations looking to harness the power of 5G. Review your carrier and provider’s security practices to thoroughly understand what equipment they use and how it is deployed so that your internal security team can understand how devices connect and how sensitive data travels through 5G networks. Understand what data is sent, received, and stored.
Additionally, 5G security only covers the network, not the devices that businesses connect to the network. Therefore, it remains important to carefully select and purchase 5G-enabled devices to avoid the risks of low-end IoT devices with little built-in security.
Michael Cobb (CISSP-ISSAP) is a well-known security author with over 20 years of experience in the IT industry.
[ad_2]
Source link


