Free WiFi networks are much more secure than they used to be. but, Public Wi-Fi is not without risks. If you do not take the necessary precautions, your traffic may still be vulnerable to interception and manipulation by attackers.
Despite the rise of HTTPS, public WiFi networks still pose some risks in 2024.
If your WiFi hotspot is compromised or manipulated by an attacker, your data and device security can be at risk.
Here’s a detailed list of the real dangers posed by public WiFi networks in 2024.
Unencrypted WiFi network
Most public WiFi networks are now password protected. That means it’s encrypted.. If you are connected to a password-protected network and someone outside your network intercepts your connection, they will not be able to decrypt your data to read it.
When you connect to a free WiFi network without a password, you are using an unsecured connection with no encryption. much less secure. In this case, everything you do online can be captured and understood by others within range.
Even when connected to a password-protected network, There are still potential risks. First, the person running the access point is trusted by the network owner to be trustworthy because they can intercept and understand user behavior.
Secondly, it is It is technically still possible to intercept and decrypt web traffic on password-protected WiFi networks. It all depends on the security of your WiFi network.
For example, in a network that uses WEP encryption, all data is encrypted with the pre-shared key (i.e. the WiFi password) used to retrieve it on the network. This means that everyone on the network can successfully decrypt everyone else’s traffic.
This is a little more difficult in WPA-PSK or WPA2-PSK networks, which use separate encryption keys for each session. However, it is not impossible. Although these keys are derived from pre-shared keys (WiFi passwords), they still carry potential risks.
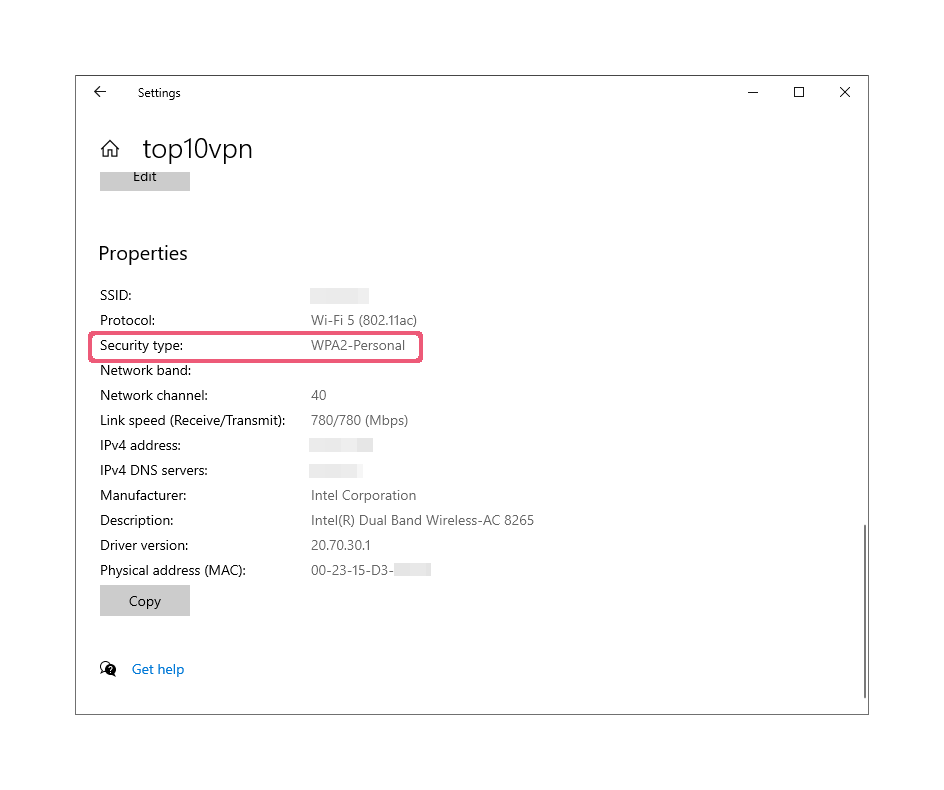
WPA2-PSK networks are more secure because they use separate encryption keys.
In a WPA Enterprise or WPA2 Enterprise network, all keys per client and per session are derived completely independently. This means it is impossible to decode other users’ traffic. In this case, the attacker would need to set up a fake hotspot to access the data.
Comparing HTTPS and HTTP websites
Most websites today use an encrypted connection called HTTPS, which uses Transport Layer Security (TLS) to protect the information passed between your device and the web server.
HTTPS is an encrypted version of the HTTP protocol, the basic Internet standard for accessing web pages. This prevents most third parties from knowing what you are doing on her website and also prevents malicious code from being injected into your web traffic.
If the website you’re visiting is HTTPS-enabled, you’ll see a padlock in the upper-left corner of your browser’s address bar.

HTTPS has made public WiFi, and the Internet as a whole, more secure. However, HTTPS does not guarantee safety online, especially on public networks. It remains vulnerable to man-in-the-middle attacks, phishing, certificate authority issues, and SSL/TLS vulnerabilities.
Most importantly, HTTPS does not protect DNS queries. DNS queries can be intercepted and manipulated to redirect you to another server under your control. For this reason, we recommend using HTTPS in conjunction with a VPN.
Expert tips: HTTPS makes sure your connection is encrypted, but it doesn’t guarantee that you’re connecting to the website you expect. If you see a padlock in your address bar, make sure it’s not directing you to another domain with a similar name.
HTTPS prevents WiFi network providers from seeing the individual pages you visit, but I still see the domain name of the website I’m visiting.
All of the most popular websites today are secured using HTTPS, but you should be wary of those that don’t. Attackers can easily monitor your activity and inject malicious code into your unencrypted (HTTP) web traffic, which is also monitored and logged by your WiFi provider. There is a possibility.
Even sites that do have secure connections may not have them set up by default. Google reports that 3 out of the top 100 non-Google websites do not have a secure connection. To stay safe on these sites, you should use a VPN or a browser extension that forces an HTTPS connection.
Worryingly, 5% of Google’s visitors don’t use HTTPS.The reason is that the devices and software they are using Too old to support modern encryption standards. If you have an older device that doesn’t support HTTPS, consider upgrading if possible.
Man-in-the-middle (MitM) attack
A man-in-the-middle (MitM) attack refers to any scenario in which a malicious third party disrupts or alters communication between two systems.
When a MitM attack occurs on public Wi-Fi, the attacker breaks the connection between the Wi-Fis. your computer And that web server I’m trying to connect to.
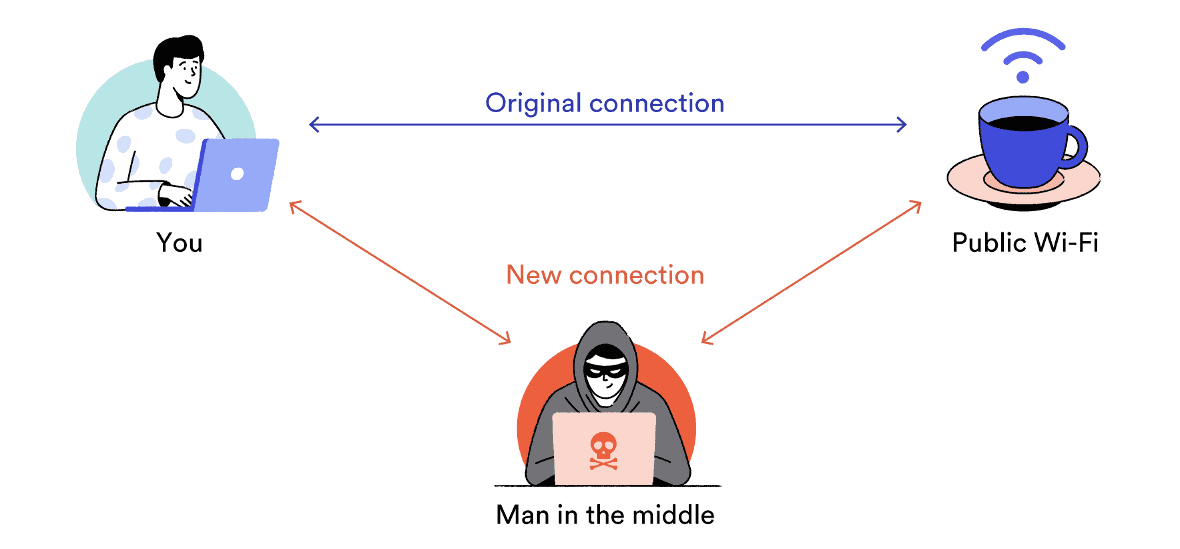
Using public WiFi networks increases the risk of man-in-the-middle attacks.
An unsecured network allows an attacker to: change the main parts of network traffic, redirect This traffic, or Inject malicious content Append to existing data packet.
Attackers can display fake websites or login forms, replace links with malicious substitutes, or add photos.
Hackers can also trick people into revealing or changing their passwords, revealing very personal information.
MitM attacks are popular among hackers. cheap, easyand effective. All a hacker needs is something like a WiFi pineapple. It’s a portable device that looks a bit like a WiFi router and costs a fraction of the price. $120.00.

of $120.00 WiFi Pineapple allows virtually anyone to exploit public networks to collect personal data.
These simple devices are Allows virtually anyone to create a fake WiFi access point and perform a man-in-the-middle attack. These are commercially available and sold at most computer hardware stores.
WiFi Pineapple can connect with hundreds of devices at once. Security researchers use it to perform attacks on public WiFi networks to test the safety of networks and learn how to protect them from attacks.
But it’s clear that it’s a dangerous tool in the wrong hands. Attackers can easily use Her WiFi Pineapple to collect sensitive personal data from unwitting public WiFi users.
WiFi Pineapple can also be used to run SSLstrip, which is software that changes secure HTTPS requests to their insecure equivalent HTTP requests.
Modern browsers are designed to allow web servers to tell the browser to use HTTPS, which helps combat this. However, this protection does not take effect until her second visit to the site.
Fake hotspots and evil twin attacks
fake hotspot or “Evil Twin attack” is one of the most common and most dangerous threats on public WiFi connections. Attackers can use these to steal unencrypted data and compromise your device.
To carry out this attack, the attacker simply imitates a public WiFi network with a seemingly legitimate name such as “Free_Cafe_WiFi” and waits for the victim to connect. Less sophisticated hackers may also choose names like “FREE INTERNET” to lure people.
The evil twin’s attack succeeds very easily. You can see this her 7 year old doing it in her 11 minutes.
WiFi Pineapple can also actively scan for SSID signals. These signals are used by your phone to find and connect. Known WiFi networks. Fake hotspots can impersonate familiar networks by copying SSID signals.
So anyone with a WiFi Pineapple. Trick your phone or laptop Just being nearby can connect you to dangerous WiFi networks. To the user, it appears that you are connecting to a network that you have previously connected to.
It’s incredibly easy to fall for fake WiFi hotspots. At the 2016 US Republican Convention, more than 1,200 people connected to unknown free Wi-Fi networks targeting names such as “I Vote Republican!” Free Internet.” as a result, 68% of users who attended the convention If you connect it, your true identity will be revealed.
These were fake networks that Avast set up in testing to make claims about public WiFi, but the consequences could have been severe.
Always be wary of automatic connections to networks, especially if you are suspicious of the network’s name or location.
DNS spoofing
DNS spoofing or “DNS cache poisoning” is a specific type of man-in-the-middle attack designed to: divert traffic Transfers from a legitimate server and redirects to a fake server. This type of attack is especially common on unprotected public WiFi networks.
Every time you connect to a website, your device sends a DNS query. When you type a URL into your browser’s address bar, we first contact you. DNS name server This will find IP addresses (e.g. 192.168.1.1) that match the domain you are looking for (e.g. example.com).
DNS spoofing is when a third party change the entry In the DNS name server’s resolver cache. This is similar to changing a phone number in a directory. If someone changes the “example.com” entry, users trying to access her website will be sent to another IP address of hers specified by the hacker.
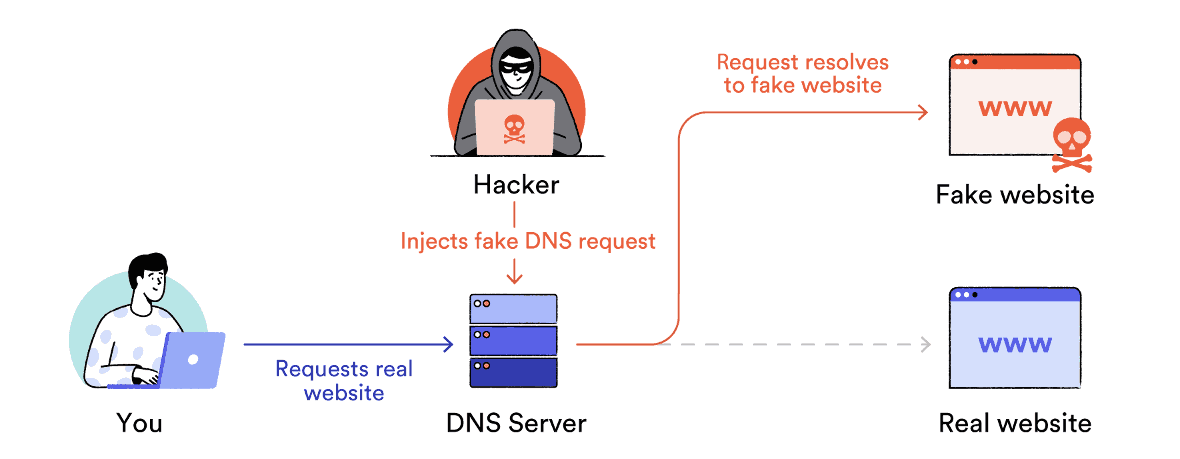
DNS spoofing works by redirecting traffic to a fake server.
In this way, an attacker can send a user to a phishing site that looks nearly identical to the intended destination. These websites are designed to trick users into entering sensitive data such as their personal information. Username and password.
Public WiFi hotspots are often run by small businesses that don’t have the technical knowledge to keep their routers completely secure. You may not have changed your default password and you may not have updated your firmware.
Hackers can install malware on unsecured routers. This malware sends all DNS queries to a malicious server. The attacker can then divert legitimate website traffic to malware or phishing websites.
session hijack
Session hijacking is another type of man-in-the-middle attack that a malicious third party can benefit from. Full control over your online accounts. Thanks to the rise of HTTPS, the risk is much lower than before.

Hackers can steal your personal information through session hijacking.
A “session” is a temporary state established between two communicating devices, such as a device and a web server. Sessions are established using authentication protocols that allow devices to recognize each other.
When you log on to a website, it assigns you a session cookie (a file containing details of your interaction with the web server). When you visit a website, the server asks your machine to authenticate itself by resending this cookie.
session hijack They copy these cookies to impersonate your device and steal your personal information..
The most valuable session cookies are those sent to users who are logged into highly secure websites, such as shopping or banking sites.
On unsecured networks, attackers can use specialized software called “session sniffers” to identify and intercept session cookies.
Session sniffing software It is illegal to use it to eavesdrop or peek at data..


