I’m fascinated by the story of how Microsoft engineers discovered a massive, well-hidden backdoor security breach that had been years in the making and nearly executed.

background
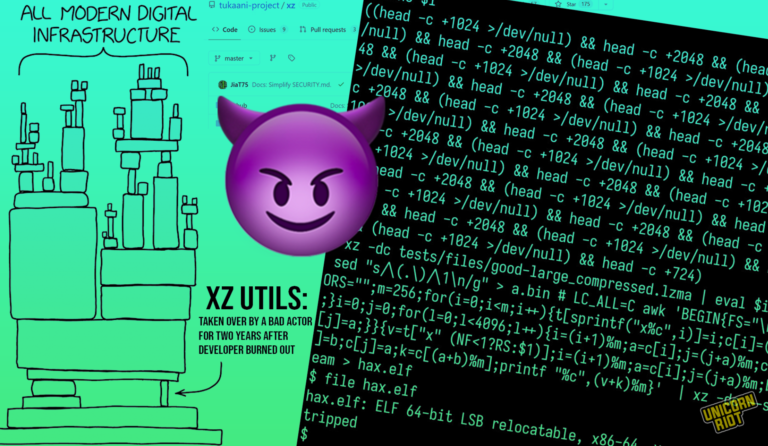
A widely used compression utility had a hidden software backdoor that allowed remote access to the entire system.
This was a years-long effort by a long-time trusted user named Jia Tan (@JiaT75). His account is now suspended everywhere.
HackerNews has an interesting excerpt.
Microsoft security researcher Andres Freund is said to have discovered and reported the issue on Friday.
The highly obfuscated malicious code was allegedly introduced by a user named JiaT75 through a series of four commits to the Tukaani project on GitHub.
long game
These open source projects are volunteer efforts. They pay nothing.
Lasse Collin (Larhzu), usually the head of the code, had been running the utility since 2009, but was suffering from burnout.
Jia Tan started contributing in the last 2-2.5 years, gained commit access about 1.5 years ago, and then gained release manager privileges.
Years of hacking plan reveals backdoor
Much of this story is very geeky and difficult to understand. Articles about the Unicorn Riot are readable.
Consider the backdoors revealed in years of hacking schemes
A fascinating but sinister software story was published on Friday. A widely used file compression software package called “xz utils” has a cleverly built-in system for backdooring shell login connections, allowing this dangerous package to reach countless internet-enabled devices. It is unclear whether there was an intrusion. It appears that Persona with this infusion has been able to play the long game and gain the trust of the official main developer, who has given them the authority to release new versions on their own.
andreas freund Reported this Friday morning on the industry security mailing listMany professionals spend their days poking under rocks and peering into the abyss of modern digital anxiety. “The upstream xz repository and xz tarball have been backdoored.” Freund wrote. It cleverly pokes holes in the SSH daemon (sshd), which is essential to modern computing at the most basic level.
Experts point out that the risk would have been extremely large if this had not been discovered. @thegrugq put it: “The ultimate goal is to be able to log into every Fedora, Debian, Ubuntu box on the Internet. If you’re not a state actor, you should be…”
Cryptographer Filippo Valsolda said: “This may be the most sophisticated supply chain attack we’ve ever reported publicly. It’s a nightmare scenario. , competent, and authorized.”
The issue was discovered after Freund noticed that a new version was slowing down tests on his PostgreSQL database and started debugging why this was happening. The backdoor caused a small but noticeable performance hit, which turns out to be a big boon for all types who are picky about benchmarks.
Ian Coldwater, a security expert in Minneapolis I got it., “Open source maintainer burnout is clearly a current security hazard. What are we doing about it?”
A June 2022 message from the original developer confessing to burnout shows how Jia Tan gained control of the software.
“I haven’t lost interest, but my ability to care is quite limited, mainly due to long-term mental health issues, but also other things. I did a little bit of work with Tan off-list, but maybe he’ll play a bigger role in the future.
It’s also good to keep in mind that this is a free hobby project.
Anyway, I can assure you that I am well aware of the issues where there is not much progress being made. The idea of finding a new maintainer has been around for a long time, as the current situation is clearly bad and sad for the project.
The new XZ Utils stable branch will be released this year with thread decoder and more, followed by several alpha/beta releases. Perhaps immediately after the 5.4.0 release will be a convenient time to change the list of project administrators. Forking is obviously another possibility, but I have no control over that. […]”Lasse Collin, xz-devel mailing list, June 8, 2022
Some observers suspect that the persona that was attacking Colin via email may also have been a puppet trying to wrest control from him. In a detailed report, ARS Technica warned that malicious actors have made many changes to the binary test files over the years, so older versions may still have security issues.
Backdoor story now revealed

upstream backdoor
“Very annoying – the supposed backdoor author has been communicating with me for several weeks trying to add xz 5.6.x to Fedora 40 and 41 because it’s a “great new feature”.. We worked with him to fix a problem with valgrind (which we now know was caused by a backdoor he added). After the embargo was inadvertently lifted last night, we had to scramble to resolve the issue. ”
“He’s been working on the xz project for two years, adding all sorts of binary test files. Honestly, given this level of sophistication, I’m not sure if xz’s old I would doubt even the version.”
us security alert
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert regarding CVE-2024-3094, a supply chain breach affecting the XZ Utils data compression library.
CISA and the open source community are responding to reports that XZ Utils versions 5.6.0 and 5.6.1 contain embedded malicious code. This activity has been assigned CVE-2024-3094. XZ Utils is data compression software and may be included in your Linux distribution. Malicious code may allow unauthorized access to an affected system.
Industry-wide calculations required
Masterdon user @glyph commented: “I really hope this will lead to industry-wide recognition of the practice of resting entire products on the shoulders of overworked workers who have a slow mental health crisis.” did. .
Here’s an interesting timeline of how this was almost implemented:
this is hero
Wow, just amazing.
It will probably take a few days for this code to be implemented.