
IntelBroker hackers claim to have infiltrated Acuity, a US federal contractor, and are selling data belonging to ICE and USCIS. The incident could potentially compromise sensitive immigration information and have national security implications.
A notorious hacker known as IntelBroker has claimed responsibility for a recent data breach that allegedly targeted Acuity Inc., a federal contractor based in Reston, Virginia. The breach resulted in the theft of sensitive data and documents from his two prominent US government agencies: U.S. Immigration and Customs Enforcement (ICE) and U.S. Citizenship and Immigration Services (USCIS).
For your information, Acuity Inc. is a federal technology consulting firm headquartered in Reston, Virginia. They provide deep industry expertise to federal agencies, particularly those focused on national security and public safety. According to the company, its core mission is to improve the ability of these agencies to plan for the future and serve their citizens, making them visible through innovative technology solutions and proven management practices. It’s about helping deliver results.
These alarming claims surfaced in recent posts on Breach Forums, a notorious cybercrime and hacker forum. Hackread.com has exclusively confirmed that the stolen data is currently for sale on its forums in the cryptocurrency Monero (XMR) for just $3,000.
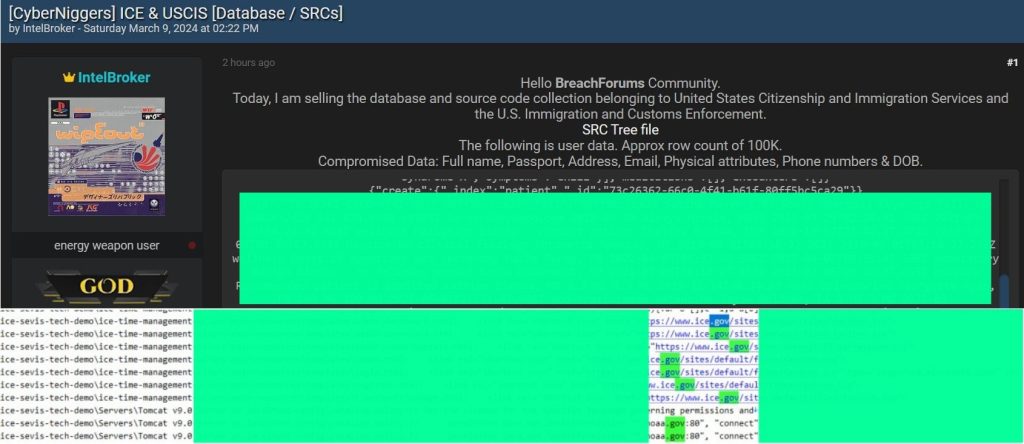
Following the announcement of the breach on the Breach Forums, IntelBroker introduced a sample of the allegedly stolen data, which allegedly contained personal and personally identifiable information (PII) of over 100,000 victims. Records on display include:
- full name
- passport
- date of birth
- telephone number
- email address
- physical address
- physical attributes.
According to the hackers, “everything belongs to U.S. citizens,” suggesting that the compromised data includes information about government employees as well as civilians.
Data confidentiality
In addition to the information available on the forum, Hackread.com also gained insight into additional sensitive data, including source code, user manuals, and confidential conversations and feedback exchanged between ICE agents and contractors. This extended to discussions about the Five Eyes alliance, Ukraine, investigative techniques used in the Russian conflict, information on terrorism-related seminars around the world, and more.
In addition, the allegedly compromised data also includes emails containing cleartext passwords for some users hosted by .GOV. However, please note that these accounts are protected by two-factor authentication (2FA) and any unauthorized access attempts will be immediately blocked until a valid code is provided.
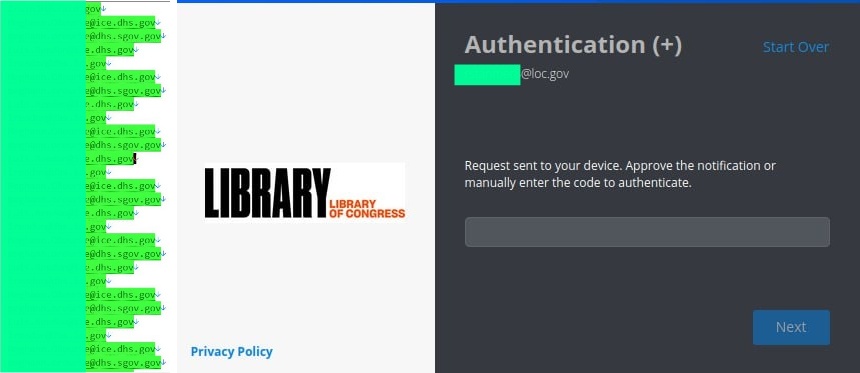
Due to the sensitive nature of this information, Hackread.com has refrained from sharing some screenshots and has edited the sample data accordingly. It is important to emphasize that Hackread.com has never attempted to access these accounts.
How did the hacking allegations come about?
In an exclusive conversation with the hacker, Hackread.com has learned that he exploited a critical zero-day vulnerability in GitHub. Despite not disclosing technical details of the proof of concept (PoC) regarding the alleged vulnerability, the hacker claims the flaw allows an attacker to steal his GitHub tokens and proceed with malicious activities. He insisted.
In response to these developments, Hackread.com has initiated contact with GitHub, ICE, USCIS, and Acuity Inc. for comment on this issue.
What is Intel Broker?
IntelBroker is known for targeting high-profile targets in the United States. Past data breaches include Los Angeles International Airport. airports, US Department of Defense documents, staffing giant Robert Half, the Facebook Marketplace database, his DARPA-related access in the General Electric breach, Weee! grocery stores and a few more.
In fact, IntelBroker was also the hacker responsible for one of T-Mobile’s data breaches, according to the US government.
The aftermath of Acuity Inc.’s alleged infringement
The fallout from Acuity Inc.’s alleged breach could have serious and long-lasting effects. If leaked data were obtained by countries the United States considers hostile, it could pose a significant national security risk. Misuse of such intelligence-related information not only jeopardizes the safety of agents and personnel, but can also jeopardize ongoing operations.
Additionally, recent events have highlighted the vulnerabilities posed by third-party contractors. Most recently, on March 4, 2024, American Express disclosed that its cardholders were affected by a major data breach originating from a third-party vendor.
In August 2023, an IT contractor employed by the Metropolitan Police suffered a cyberattack that affected more than 50,000 Met Police personnel.
In September 2023, a third-party contractor experienced a data breach that affected more than 8,000 Greater Manchester Police officers. In October 2023, another contractor accidentally published its database, resulting in the leaking of confidential information about half a million Irish police vehicle seizure records.
Related topics
- US government’s secret terrorist watch list, 2 million records published online
- Chinese group Storm-0558 European government emails hacked, Microsoft
- Adobe ColdFusion flaw used by hackers to access US government servers
- Traffic signs near ICE headquarters are hacked and display the message “ICE is abolished”
- Norwegian researchers reveal how US companies collect location data


