Public WiFi networks are ubiquitous these days, with public WiFi networks installed in almost every business, including coffee shops, hotels, and supermarkets. For many of us, asking for the WiFi password may be the first thing we do when we sit down to eat. While this is certainly convenient, don’t underestimate the dangers of public WiFi.
In this article, we will explain what these dangers are, what attack vectors they can use against users, and finally, how to protect yourself from dangers and prevent attacks if you frequently use open WiFi networks. I’ll explain how.
Is it dangerous to use public Wi-Fi?
Yes and no. If you frequently connect to public WiFi networks without taking any precautions and with little regard for the reliability of the hotspots you use, you are absolutely putting yourself at serious risk. However, there are simple precautions you need to take to make public WiFi completely secure, so you can connect to public hotspots with confidence.
What are the risks of using unsecured WiFi?
Unsecured or public WiFi networks come with many risks. Even if the network in question is a secure public WiFi hotspot, anyone who wants to access it can gain access by simply asking one of your employee’s girlfriends for the password.
To make matters worse, many networks open up their WiFi settings, allowing anyone connected to gain administrative access to your router.
With this access, there are a variety of ways that cybercriminals can take advantage of unsuspecting users who are simply browsing the web, most often in the form of what is known as a “man-in-the-middle” attack.
man-in-the-middle attack
Attacks that exploit the weak security of public WiFi generally fall into the category of man-in-the-middle attacks. This literally means that the attacker is positioned between you and the server you are trying to access.
This allows attackers to capture all traffic and use it to steal personal information, swipe payment details such as credit cards, or manipulate data packages to inject malware or spyware onto your device. You can even install it.
network snooping
Monitoring incoming and outgoing traffic on a public network is a type of man-in-the-middle attack that is surprisingly easy to perform.
Anyone can download a tool like Wireshark, and with a few YouTube tutorials, it’s all you need to see exactly what you’re doing on your laptop during your morning browsing at the coffee shop. are all available.
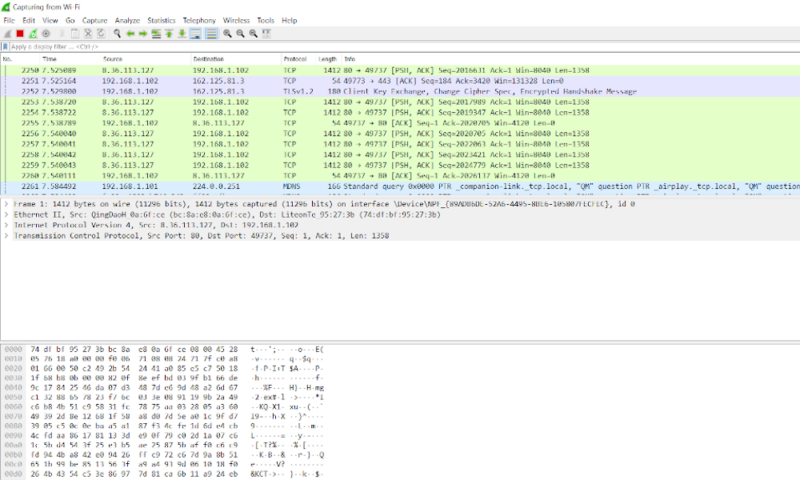
This means that any information you submit, such as credit card details and passwords, is exposed to an attacker who can easily access the account you are signed into and the payment details you use.
Distribution of malware
Another common attack method against public WiFi networks is known as malware injection. As mentioned above, attackers can use snooping software to inspect data sent to and from your device, but this is just the tip of the iceberg. Not only can they see your traffic, but they can also manipulate it.
In layman’s terms, this essentially intercepts a web server’s response before it reaches the user, injects hidden malicious code that runs when the page is opened on the device, and sends it on its way. I will do it. If an attacker does this correctly, they probably won’t even realize anything happened until it’s too late.
Encrypting your traffic is generally sufficient to prevent this type of attack from occurring. However, as mentioned above, an attacker may have access to the server credentials of the site you are visiting, allowing them to completely bypass encryption and access your browsing traffic even over a secure connection. Malware can be inserted.
Dangerous WiFi hotspots
Unfortunately, cybercriminals operating in legitimate WiFi hotspots is just one of the risks you can face when using public connections.
An even bigger risk to safety are malicious hotspots set up to trick users into accessing them. This is usually done by creating an insecure hotspot with the name of a nearby business such as a restaurant, cafe, or hotel, and users connect there without realizing the danger.
You can protect yourself from this scenario by always asking your employees if the WiFi hotspot is legitimate, but there’s no guarantee that your employees are aware of the imposter. In fact, your company’s employees may even be using a compromised WiFi network without realizing there’s anything wrong with it.
In this scenario, the attacker has complete control over the hotspot and can serve malicious ads that carry spyware or malware, replace the websites you want to visit with completely fake ones, or collect your credentials. More attack vectors are available, such as Please apply for various services.
Is HTTPS secure on public WiFi?
In theory, HTTPS can protect against man-in-the-middle attacks when connecting to public networks. Learn more about HTTP and HTTPS. Simply put, HTTPS protects your traffic by encrypting it and using TLS to verify the other side of the transaction.
This means that the “man in the middle” cannot decrypt encrypted data because he does not have the necessary credentials to decrypt it.
However, this is not foolproof and there are several ways around this, including changing the redirect from HTTPS to HTTP and submitting a bad certificate. The browser will detect that the certificate is invalid, but most users usually ignore this type of warning.
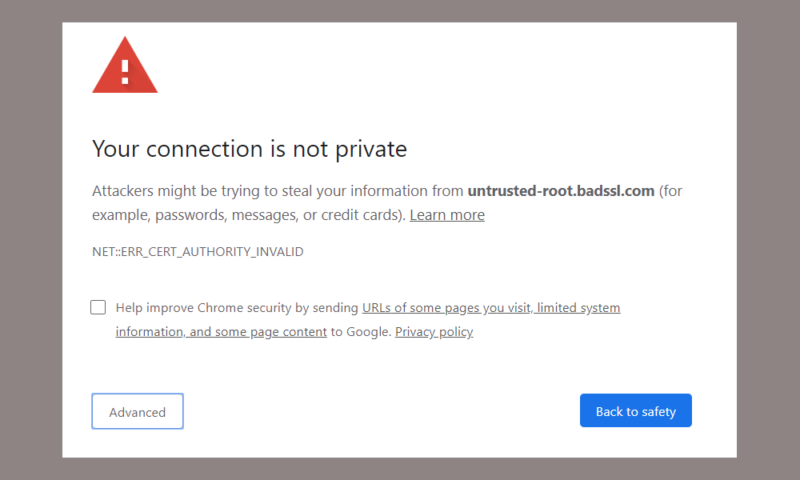
Even if you heed and heed these warnings, you may still be at risk. If an attacker already has the private key belonging to the server you think you’re connecting to, they have no problem creating a fake certificate that your browser won’t warn you about.
What’s more, by hacking and “owning” the router that transmits the WiFi signal at your workplace, an attacker could collect your encrypted traffic over time.
Even if all the data is encrypted, unless the server owner implements full forward secrecy protection, a security breach in the future and an attacker gaining access to the server’s private key could be All collected data may be retroactively decrypted.
How to stay safe on public WiFi
At the end of the day, there’s only one good way to stay safe while using public WiFi networks. That means using the best VPN for public WiFi.
A Virtual Private Network (VPN for short) protects you by creating a “tunnel” for all your traffic, and is protected by end-to-end encryption.
Rather than sending traffic directly from your device to a server, a VPN routes all your traffic through its own servers ahead of time. This additional security prevents man-in-the-middle attacks as attackers cannot see any of your traffic, even though you are connected to the same public WiFi hotspot.

However, not all VPNs are created equal. While the best VPNs will ensure that your traffic is secure and encrypted, making it impossible for attackers to decrypt it, other VPNs lack certain security features or use weak encryption, making it difficult to use a VPN. The additional security you gain from using it may be compromised. that. To better understand how secure your VPN is, read our encryption explanation.
Be sure to read our ExpressVPN review for our picks for the top VPNs. If you’re still not sure, check out our NordVPN review and Cyberghost review. These two providers round out our top three favorite VPNs.
final thoughts
Here’s everything you need to know about security when using public WiFi and how to stay secure while using it. As mentioned earlier, there’s no better way to protect against attacks over public Wi-Fi than with a VPN, so download and install one of the best VPNs to keep your security intact.
If you primarily use your phone to browse when connected to public WiFi networks, be sure to read our guide to the best VPNs for mobile. Other than using a VPN, there’s not much you can do to prevent someone from using your local business’s WiFi to capture sensitive data or install malware on your phone, tablet, or laptop.
What do you think of our summary of the dangers associated with public Wi-Fi? Do you understand the serious risks and how to protect yourself from them, or do you think this is all just unwarranted paranoia? Let us know in the comments section below. thank you for reading.


